
Early yesterday a massive new ransomware infection began to spread in a method very similar to the WannaCry virus. This one, however, is a little bit different from WannaCry. Petya or NotPetya seems to take ransomware to the next level by infecting the Master Boot Record (MBR). By going this route, the ransomware deletes any encryption keys resident in memory when the system is rebooted, which makes recovery of the files unlikely.
How it is spreading?
Initial reports indicate that an accounting software firm in Ukraine was compromised, their updater was utilized to push the malware out to customers. Once a customer system is infected, the malware does a couple of things:
- It pulls down additional tooling for lateral spread.
- it begins to encrypt files on the infected system, then schedules a task to restart the system in an hour.
Where WannaCry used only EternalBlue (MS17-010) for lateral spread, Petya uses a variety of tools, many that penetration testers like me use for lateral movement within an environment.
The initial dropper will pull down a version of PSExec, a sysinternals tool from Microsoft that can be used for system administration, and a custom piece of malware that utilizes many features within mimikatz that can scrape clear text passwords out of memory. To spread within an environment, the malware first tries the EternalBlue exploit; if systems are not vulnerable, it will utilize PSExec and WMIC after leveraging passwords scraped form memory to infect other systems.
What can companies do?
Based on some analysis from Dave Kennedy over at Binary Defense, this very specific variant can be stopped if you block “C:\Windows\perfc.dat” from writing or executing using something like Microsoft Software Restriction Policy.
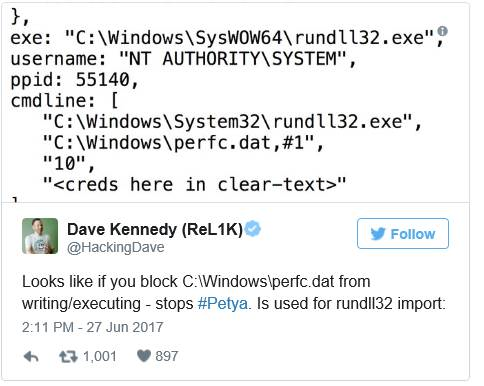
But this will only defeat this specific variant from spreading. The other thing to do is ensure that EternalBlue (MS17-010) is patched.
Long term, there are several things to do:
- Deploy a solution like LAPS that can manage separate local admin passwords per deployed system.
- Remove local administrator rights from common users, this will block the ability for Petya to collect administrator credentials from memory.
- Use Windows Firewall to block system-to-system communication for workstation subnets. There is typically no reason for two workstations to talk to each other; blocking communication can significantly reduce lateral spread.
- Look for behavioral-based endpoint controls to help catch this. LRS has partnered with Cybereason, who created a Endpoint Detection and Response (EDR) tool that can detect and prevent Petya as well as other types of ransomware. Cyberason also provides a free software product called RansomFree that can be deployed to detect and prevent this issue.
The last question I hear a lot is “Should we pay the ransom?” Reports indicate that the German email provider hosting the email account used for requesting unlock keys has been blocked, so the attackers are no longer able to communicate unlock keys with the victims who pay and request them.
To get more information about how to protect yourself against ransomware please reach out to your LRS IT Solutions Account Executive.
About the author
Greg Hetrick is our Security Solutions Technical Advisor and Penetration Testing Lead, and he focuses on helping customers identify gaps and achieve security goals. Prior to joining LRS Greg held roles as a red and blue team leader in a large financial services company and a large academic medical research hospital. He holds multiple certifications in the area of Information Security including: CISSP, GISP, GPEN, GXPN, and CISSP